Client-side Trace for SQL*Plus
EVENT_25701=15EVENT_25703=15
SQL> alter system set events 'TRACE[PRIVS] DISK=HIGHEST’;
SQL> alter system set events 'TRACE[AUTH] DISK=HIGHEST';
SQL> alter system set events 'TRACE[TOKEN] DISK=HIGHEST';
SQL> SELECT FROM V$DIAG_ALERT_EXT ORDER BY originating_timestamp desc;
SQL> SELECT * FROM UNIFIED audit_trail ORDER BY event_timestamp desc fetch first 100 rows only;
SQL> CREATE AUDIT POLICY ORA LOGON_SUCCESSES ACTIONS LOGON;
SQL> AUDIT POLICY ORA_LOGON_SUCCESSES WHENEVER SUCCESSFUL;
PDB1 =
(DESCRIPTION=
(ADDRESS=(PROTOCOL=TCPS)(HOST=hrdb.dbauthdemo.com)(PORT=2484))
(SECURITY=
(SSL_SERVER_DN_MATCH=TRUE)
(WALLET_LOCATION=SYSTEM)
(TOKEN_AUTH=AZURE_INTERACTIVE)
(TENANT_ID=7f4c6e3e-a1e0-43fe-14c5-c2f051a0a3a1)
(CLIENT_ID=e5124a85-ac3e-14a4-f2ca-1ad635cf781a)
(AZURE_DB_APP_ID_URI=https://dbauthdemo.com/16736175-ca41-8f33-af0d-4616ade17621)
)
(CONNECT_DATA=
(SERVER=DEDICATED)
(SERVICE_NAME=pdb1)
)
)
SQL> connect (DESCRIPTION=(ADDRESS=(PROTOCOL=TCPS)(HOST=hrdb.dbauthdemo.com)(PORT=2484))(SECURITY=(SSL_SERVER_DN_MATCH=TRUE)(WALLET_LOCATION=SYSTEM)(TOKEN_AUTH=AZURE_INTERACTIVE)(TENANT_ID=7f4c6e3e-a1e0-43fe-14c5-c2f051a0a3a1)(CLIENT_ID=e5124a85-ac3e-14a4-f2ca-1ad635cf781a)(AZURE_DB_APP_ID_URI=https://dbauthdemo.com/16736175-ca41-8f33-af0d-4616ade17621))(CONNECT_DATA=(SERVER=DEDICATED)(SERVICE_NAME=pdb1)))
- Invalid username or password provided
- The server side configuration of the target database of the client connection (CDB or PDB) may not yet be configured for Entra Integration including setting IDENTITY_PROVIDER_TYPE to AZURE_ID and applying Entra ID integration to IDENTITY_PROVIDER_CONFIG. If application_id_uri of the IDENTITY_PROVIDER_CONFIG is incorrect or even if it includes an extra character like a space at the end will cause error ORA-01017.
- The connection string or TNS entry of the client may not include all requisites for Entra ID integrated database
- The database server fails to connect to login.microsoftonline.com or login.windows.net when retrieving keys to check the authenticity of the access token. This may be a firewall block.
- If logging in with device code flow, "Allow public client flows" needs to be set to "yes" in database client app registration in Authentication section
- The length of the TLS certificate common name (CN) value exceeds 64 characters. This is a constraint imposed by OpenSSL conformance with RFC 5280.
- Use the following to determine if IDENTITY_PROVIDER_TYPE is set to AZURE_ID:
SQL> SELECT NAME, VALUE FROM V$PARAMETER WHERE NAME='identity_provider_type';
- Use the following to determine if IDENTITY_PROVIDER_CONFIG has the correct values for tenant_id, application_id_uri (e.g. database app URI), and app_id (e.g. database app registration's application ID).
SQL> SELECT NAME, VALUE FROM V$PARAMETER WHERE NAME='identity_provider_config';
- The tnsnames.ora file does not exist in <odb_client_base>\network\admin or that the specified database does. Note that you can specify TNS_ADMIN=\<path> to specify the folder path to the tnsnames.ora file
- The requested database does not exist in the tnsnames.ora file.
- The SQL*Plus command cannot connect to the host specified in the TNS or connect string entry
- Check network firewall or host-based firewall ingress rules allow the host of the database client to connect to the host of the database server
- Check the network firewall or host-based firewall egress rules do not allow the database client or server to connect to the database server's host
- Oracle database listener is not running or ingress firewall rules (network or host-based) are blocking access to the database port.
- Can’t lookup specified connect string. Check name service resolution in tnsnames.ora or directory service
- Make sure TNS_ADMIN is set to the directory where tnsnames.ora exists
- You get the following Microsoft Entra ID error when you specify an invalid client ID.
- Occurs if you specify PROTOCOL of TCP instead of TCPS in connect string or TNS entry
- Occurs when incorrect SERVICE_NAME value is specified in connect string or TNS entry
- In the case of SQLDeveloper, this can occur if the SQLDeveloper product.conf configuration file does not have all of the requisite OJDBC extension libraries required for Entra ID integration. See this blog post (https://www.braddiggs.com/2025/04/entra-id-integration-for-sqldeveloper.html) for details on how to configure SQLDeveloper for EntraID integration
- This can result from using a version of the SQL*Plus client earlier than 23.7.
- Note that if the connect string or TNS entry specifies TOKEN_AUTH=AZURE_DEVICE_CODE , this may indicate that AZURE_DEVICE_CODE is not yet supported
- Occurs when attempting to connect via thin client with TOKEN_AUTH=AZURE_DEVICE_CODE and the previous authentication was successful but failed to get token (Error: ORA-18726)
- All Entra ID integration connections between Oracle database client require encrypted TLS connection with SSL_SERVER_DN_MATCH=TRUE
- If using file-based access token acquisition and refreshing, the token is not present, invalid or expired
- If using memory-based access token acquisition and refreshing, the token may not have been passed because of an issue with TLS configuration setup between the database client and database server.
- Use client and server side tracing to ascertain root cause.
- OCI driver (e.g. sqlplus) or JDBC-thick driver version used is not supported. SQL*Plus 19.18 or newer is required
- If connecting with device code flow, this error is returned if running DBEE 23.8 or prior. DBEE 23.9 and newer are the only versions that supports device code flow.
- JDBC-thin driver appears to only work with 23.7 or newer
- Occurs when CLIENT_ID is invalid format or bad value in connect string or TNS entry
- Occurs if the TENANT_ID is incomplete or invalid format in the connect string or TNS entry
- Occurs when no client credentials have been entered for TOKEN_AUTH=AZURE_SERVICE_PRINCIPAL
- Occurs when pop-up browser connection to https://login.microsoftonline.com times out after 60 seconds
- Test connection multiple times from your computer to Microsoft login with:
- Linux: curl -ksL https://login.microsoftonline.com/
- Windows Powershell: Invoke-WebRequest -Uri https://login.microsoftonline.com
- Note that web connection test may require going through a web proxy if direct outbound connections are not permitted
- If connection is successful some of the time, there may be a routing or firewall issue between your computer and Microsoft's login page
- If connection fails every time, there is likely either a firewall constraint, routing issue or Microsoft login may be temporarily down
- In Microsoft Terminal Services environments like Microsoft RDP or Citrix, the ODB client redirect to localhost (127.0.0.1) may not be connecting to the user's session real localhost (127.0.0.2-n). The respective terminal services solution will need to be configured to connect the two for the requesting client application. In this case determine what port that the web browser used to connect to localhost after successful EntraID authentication (typically localhost:8400 but can be other number) and then use (netstat -ano | findstr "<port>") to find the process that is trying to connect to that port. Note that both the web browser (Edge or Internet Explorer by default in Windows Server depending on version) and the identified process will need to be added to the Windows or Citrix policy for connecting the virtual localhost (127.0.0.1) and real user session localhost (127.0.0.n). Here is a screenshot from the Citrix policy:
- This error occurs if you have not specified the correct TENANT_ID in the connect string or TNS entry
- Entra ID authentication attempt either timed out or failed to authenticate properly
- Occurs when incorrect CLIENT_ID value is specified in connect string or TNS entry
- WALLET_LOCATION of the connect string or TNS entry has specified a wallet path for which no wallet exists
- If you’ve specified the non-secure port number (Default: 1521) instead of the secure port number (Default: 2484) in the connect string or TNS entry
- Note that the default autonomous database uses port 1521 for secure port
- The database server may have not yet set the wallet_root directory
- Check to make sure that the wallet has been copied to the PDB GUID directory ($WALLET_ROOT/$pdbguid/tls) on the database server
sqlplus / as sysdba
SQL> alter system set wallet_root='/u01/app/oracle/19c/wallet_root' scope=spfile;
SQL> shutdown immediate;
SQL> quit;
lsnrctl stop
lsnrctl stop
sqlplus / as sysdba
SQL> startup;
SQL> alter pluggable database all open;
SQL> alter system register;
SQL> quit;
- The connect string or TNS entry host value does not match the certificate CN value as reported by openssl s_client.
$ echo | openssl s_client -connect hrdb.dbauthdemo.com:2484 2>&1 | openssl x509 -noout -text | egrep -i "DNS|subject"
Subject: CN=hrdb.dbauthdemo.com
Subject Public Key Info:
X509v3 Subject Alternative Name:
DNS:hrdb.dbauthdemo.com, DNS:www.hrdb.dbauthdemo.com
X509v3 Subject Key Identifier:
- Occurs the SSL_SERVER_CERT_DN value of the connect string or TNS entry does not match the certificate subject or subject alternative name (SAN) entries of the certificate
- You can use the openssl command of a Linux host to ascertain the certificate and SAN entries of the database server with:
$ echo | openssl s_client -connect hrdb.dbauthdemo.com:2484 2>&1 | openssl x509 -noout -text | egrep -i "DNS|subject"
Subject: CN=hrdb.dbauthdemo.com
Subject Public Key Info:
X509v3 Subject Alternative Name:
DNS:hrdb.dbauthdemo.com, DNS:www.hrdb.dbauthdemo.com
X509v3 Subject Key Identifier:
- Certificate CN value may be greater than 64 characters. 64 characters are the maximum length for Public Key Infrastructure (PKI) deployments as specified in RFC 5280. You can determine the character length of the CN value with "wc -c" command. For example:
echo hrdb-hbl12-scan.privatesubnet1158-mycompanytenancy.dbauthdemo.com|wc -c
66
- This error can be caused by the signing certificate authority not being present in the client host certificate authority trust store
- Use orapki on the database host to display the trusted certificate subject and confirm that this trusted certificate is in the client host
- orapki wallet display -complete -wallet $WALLET_ROOT/tls -pwd <wallet_password>
- In Windows client, run mmc, add “Certificates” snap-in, look up “Trusted Root Certification Authorities” to see if the DN o the certificate authority matches the subject of the same certificate authority from orapki display
- In Linux, return all of the CA certificate subjects with: openssl crl2pkcs7 -nocrl -certfile /etc/pki/tls/certs/ca-bundle.trust.crt | openssl pkcs7 -print_certs -noout
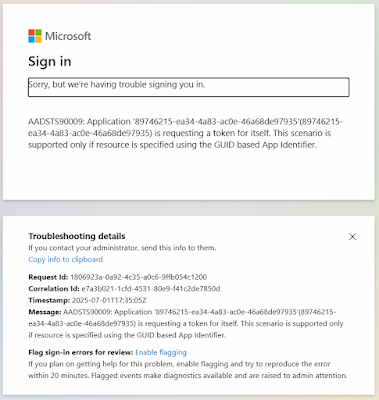
Error: AADSTS90009: Application '...'(...) is requesting a token for itself. This scenario is supported only if resource is specified using the GUID based App Identifier.
- This error is caused by specifying the database server's web Application (client) ID for the value of the CLIENT_ID of the connect string or TNS entry. Here is a sample screenshot of this error.
- Possible routing or firewall constraint due to client host being on IPv6 rather than IPv4 when connecting over VPN to the corporate network. If the customer disables IPv6 of the client host's network interface and makes sure IPv4 is enabled before connecting over VPN to the database server's network, this may resolve the issue. Enabling client side tracing revealed the following pattern in the trace file that seems to indicate that the client is attempting to connect to Entra ID using the IPv6 address and is being blocked by firewall or something along those lines:
nttcni: trying to connect to socket 1412.
...
ntt2err: soc 1412 error - operation=1, ntresnt[0]=516, ntresnt[1]=13, ntresnt[2]=0
...
nsopen: unable to open transport
...
nsc2addr: (ADDRESS=(PROTOCOL=tcp)(HOST=2603:1036:3000:18::2)(PORT=443))
Client Error Code: 53003 - Your sign-in was successful but you don't have permission to access this resource.
- There are several occurrences of this error available on the internet that all point to a restriction of the Entra ID Conditional Access Policy. In one customer case, this was a restriction that does not allow contingent workers to use the Entra ID web application registrations that represent the Oracle database servers. The Entra ID administrator had to explicitly grant that permission for this web application for contingent workers. Microsoft recommends using the following troubleshooting guides for Conditional Access Policies:
- https://learn.microsoft.com/en-us/entra/identity/conditional-access/troubleshoot-conditional-access
- https://learn.microsoft.com/en-us/entra/identity/conditional-access/concept-conditional-access-conditions
Client Error Code: 18 - REST API call failed! REST API call failed to get public key from endpoint.
- In the last step of the authentication flow, the database server connects to Entra ID to retrieve the current keys for validating the authenticity of the access code. This is the error returned when the database server fails to connect to Entra ID to retrieve the keys. Test connecting to Entra ID with the following command according to the operating system of the host on which the database server is running and based on the result you will either need to resolve a routing issue or firewall egress rule:
- Linux: curl -ksL https://login.microsoftonline.com/common/discovery/v2.0/keys
- Windows Powershell: Invoke-WebRequest -Uri https://login.microsoftonline.com/common/discovery/v2.0/keys
- NetCat: nc -zv login. windows.net 443
- Python: python -c 'import requests;response = requests.get("https://login.microsoftonline.com/common/discovery/v2.0/keys"); print(response.text)'
- Python3: python3 -c 'import requests; response=requests.get("https://login.microsoftonline.com/common/discovery/v2.0/keys");print(response.text)'
- Perl: perl -MLWP::UserAgent -E 'my $ua = LWP::UserAgent->new(ssl_opts => { verify_hostname => 0 }); my $res = $ua->get("https://login.microsoftonline.com/common/discovery/v2.0/keys/"); print $res->is_success ? $res->decoded_content : $res->status_line;'
It could also be retrieving the keys from https://login.windows.net/common/discovery/keys
If any of these commands returns an error indicating certificate verify failure means that the operating system trust store does not include the certificate chain used by Microsoft. For example, python returns "SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed".
Note that if the host OS of the database server is old or does not include a truststore, you may need to update the OS trust store with all of the current root and intermediate certificate chains from Microsoft found at https://learn.microsoft.com/en-us/azure/security/fundamentals/azure-ca-details?tabs=root-and-subordinate-cas-list.





No comments:
Post a Comment